Are Screenshots Sufficient Evidence?

,
Timothy R. Primrose, Mobile Forensic Analyst
Text messages, photographs, and call lists accessed directly from a cell phone reveal only a fraction of usage data stored within the device. Accessing additional data, unattainable by scrolling through the device, requires sophisticated software that collects a detailed timeline of phone events. This metadata, or data that gives information about other data, can assist in distinguishing between, whether a text message was received or was received and read.
The image on the left provides a text message conversation snapshot displayed on a cell phone. The image on the right shows data about the same conversation, provided by a forensic extraction.
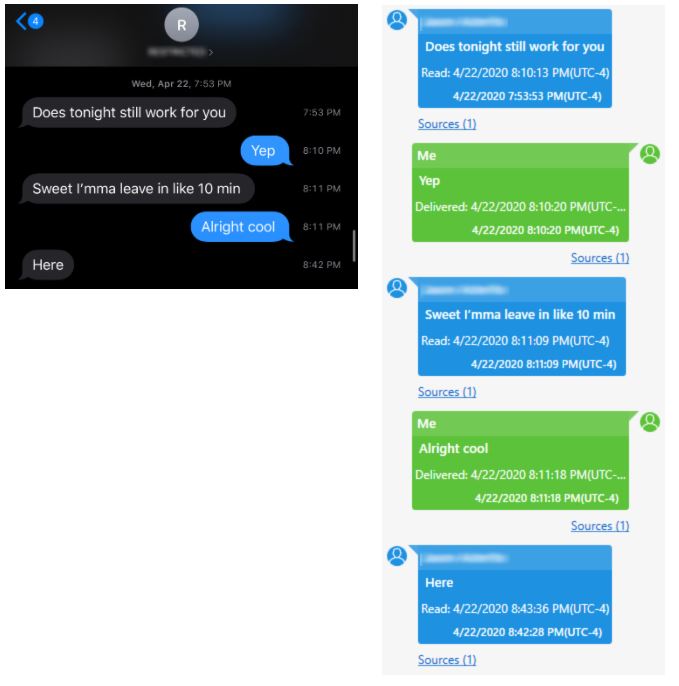
The data accessed from a forensic extraction (image on the right) offers conversation bubbles displaying the same messages from the external party and device user; however, the timestamps include the number of seconds passed in the given minute that a message was sent or received, as well as the time zone and the year. Received messages include two timestamps: one which conveys when the text message was received (the bottom timestamp located in the blue conversation bubbles), and the other conveys when the text message was read or opened (the top timestamp located in the blue conversation bubbles indicated by “Read:”). Delivered messages also include two timestamps, note in the reference text messages that the two timestamps displayed in the green conversation bubbles are identical. This is because the message was sent immediately. If there is poor network connection, messages may send at a later time. In this case, the bottom timestamp would show when the text message was intended to be sent, and the top timestamp would indicate when the message was delivered.
In a recent investigation where distracted driving was suspected after a hit-and-run collision, the screenshots of text messages seen in the left image were reviewed as evidence. The timestamp indicated that a message was received around the time that the incident occurred, potentially causing the driver to become distracted and lose control of their vehicle. The data received from the forensic extraction on the right, showed that the message in question was not read until after the incident occurred.
Screenshots cannot authenticate through a validated forensic software that provides repeatable analysis methods. Screenshots are also susceptible to alteration, as photo editing tools like Photoshop can be used to change messages to have different timestamps or content. In contrast, Data extracted from a cell phone, via validated forensic software, is write-protected, meaning that the Data cannot be manipulated or changed. In the event that text message Data is utilized as evidence, it is imperative that the Data is procured in a forensically sound manner.
Timothy R. Primrose, Mobile Forensic Analyst with DJS Associates, Inc., can be reached via email at experts@forensicDJS.com or via phone at 215-659-2010.
Tags: Mobile Forensic Analyst | Timothy R. Primrose


