Gone Phishing

Timothy R. Primrose, Mobile Forensic Analyst Millions of people have cell phones and use them to send text messages and browse the web daily. Many of these people have also…
It’s Spooky Season

Timothy R. Primrose, Mobile Forensic Analyst It’s spooky season, and while you might be afraid of ghouls and vampires, you might be missing out on a scarier thing: hacking. Depending…
CSAM

Apple is working to fight against child sexual abuse by scanning photos that are uploaded to iCloud for CSAM (child sexual abuse material). Apple is also trying to battle the…
Cell Phone Evidence Repair
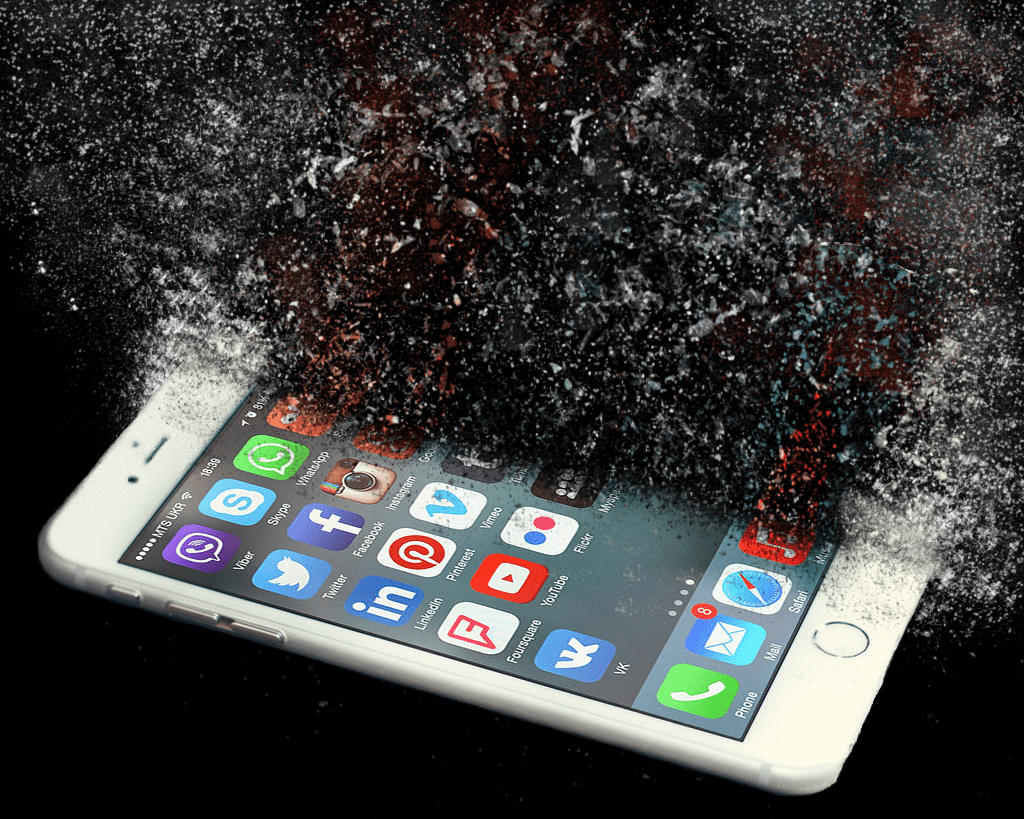
Timothy R. Primrose, Mobile Forensic Analyst There are three components of a cell phone that need to be functioning in order to extract data from the device: the screen, the…
Apple’s Health Application

Timothy R. Primrose, Mobile Forensic Analyst Apple’s health application monitors and documents a user’s day to day activity in detail. Some data is collected by the iPhone, while other data…
Are Screenshots Sufficient Evidence?

Timothy R. Primrose, Mobile Forensic Analyst Text messages, photographs, and call lists accessed directly from a cell phone reveal only a fraction of usage data stored within the device. Accessing…
Tracking Uber Rides

Timothy R. Primrose, Mobile Forensic Analyst There are approximately three billion smartphone users worldwide. Smartphones can provide users with turn by turn directions to a given destination via applications such…
Screen Time

Timothy R. Primrose, Mobile Forensic Analyst Screen time across multiple devices has heavily increased since strict guidelines calling for social distancing began in March of 2020. If you own an…
So You Think You Know All That Cellphones Can Do

Timothy R. Primrose, Mobile Forensic Analyst The typical thought process for involving cell phone data relevant to a collision in a forensic investigation follows something like, “was the person texting…


